Utilizing Morse Code to Evade Signature Based Detection Systems
Por um escritor misterioso
Last updated 07 julho 2024


Multifunctional Conductive Double-Network Hydrogel Sensors for Multiscale Motion Detection and Temperature Monitoring

Utilizing Morse Code to Evade Signature Based Detection Systems –
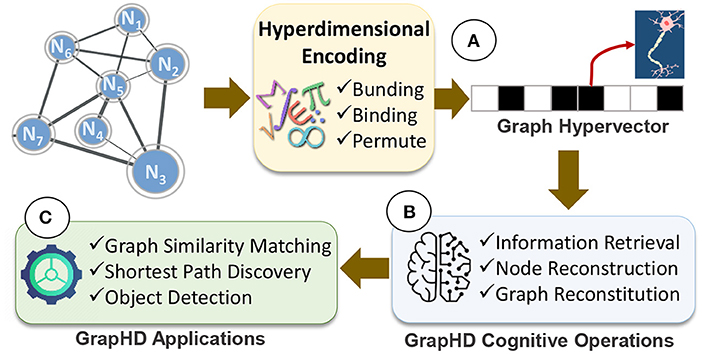
Frontiers GrapHD: Graph-Based Hyperdimensional Memorization for Brain-Like Cognitive Learning

The invariant in the form of a predetermined deterministic

The average loading time for news sites using CovertCast over .
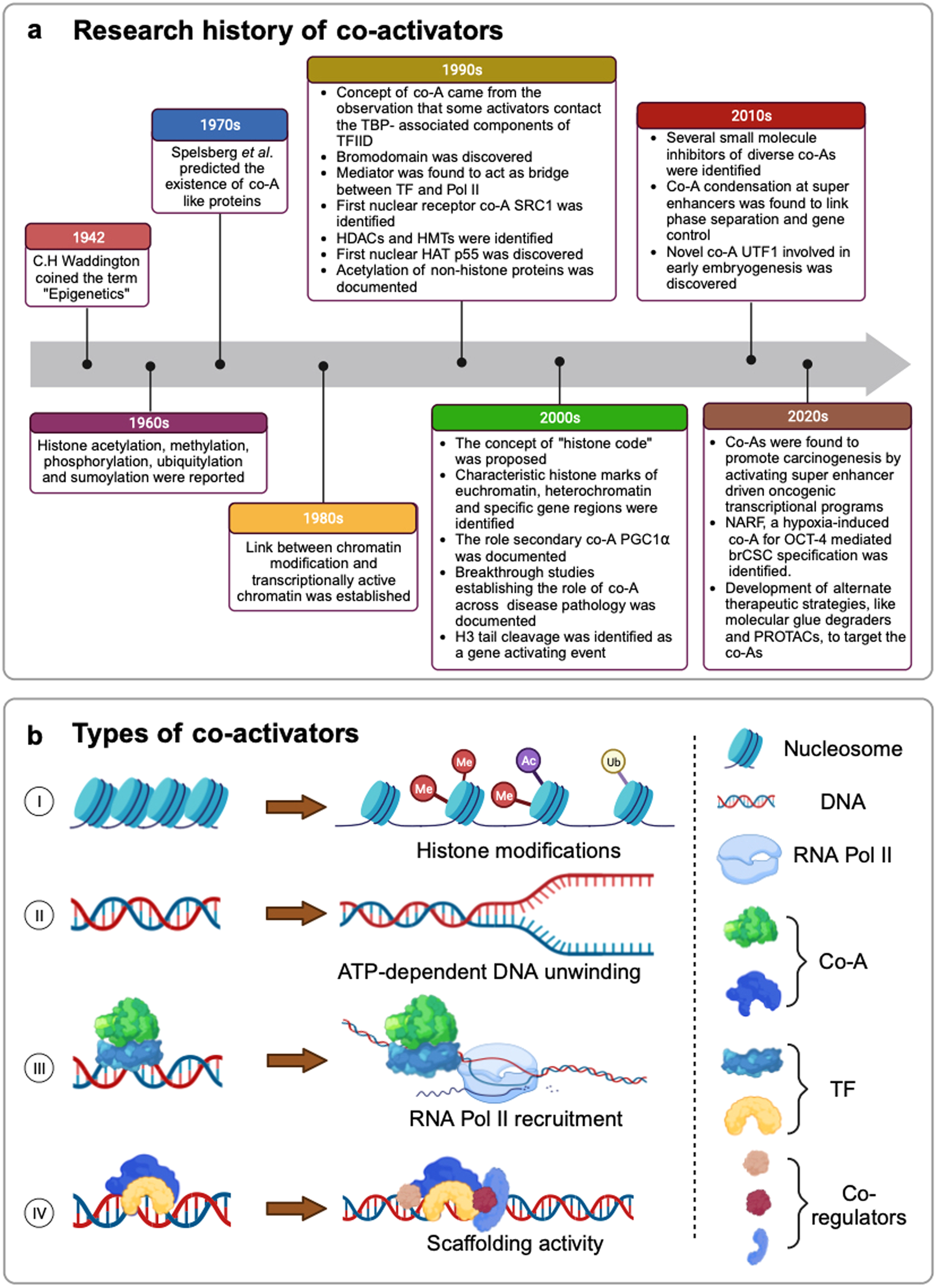
Transcriptional co-activators: emerging roles in signaling pathways and potential therapeutic targets for diseases

Volume 2-issue-6-2037-2039

Threat Actors Found Using Encrypted RPMSG Messages in Microsoft 365 Phishing Attacks

PDF] Morse code based Secured Authentication System using Eye Blink through Haar Cascade and Facial Landmark Algorithm
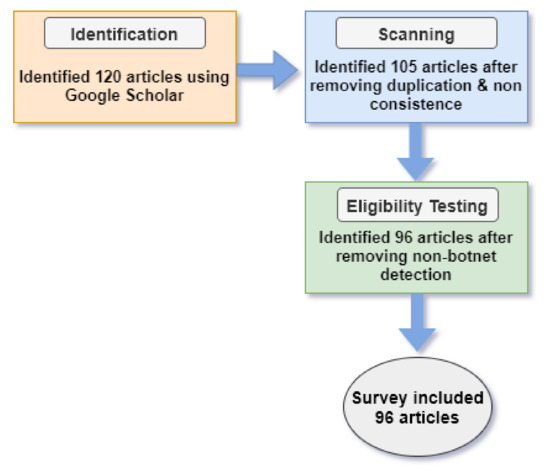
Symmetry, Free Full-Text

Blind Spot: A Braille Patterned Novel Multiplex Lateral Flow Immunoassay Sensor Array for the Detection of Biothreat Agents
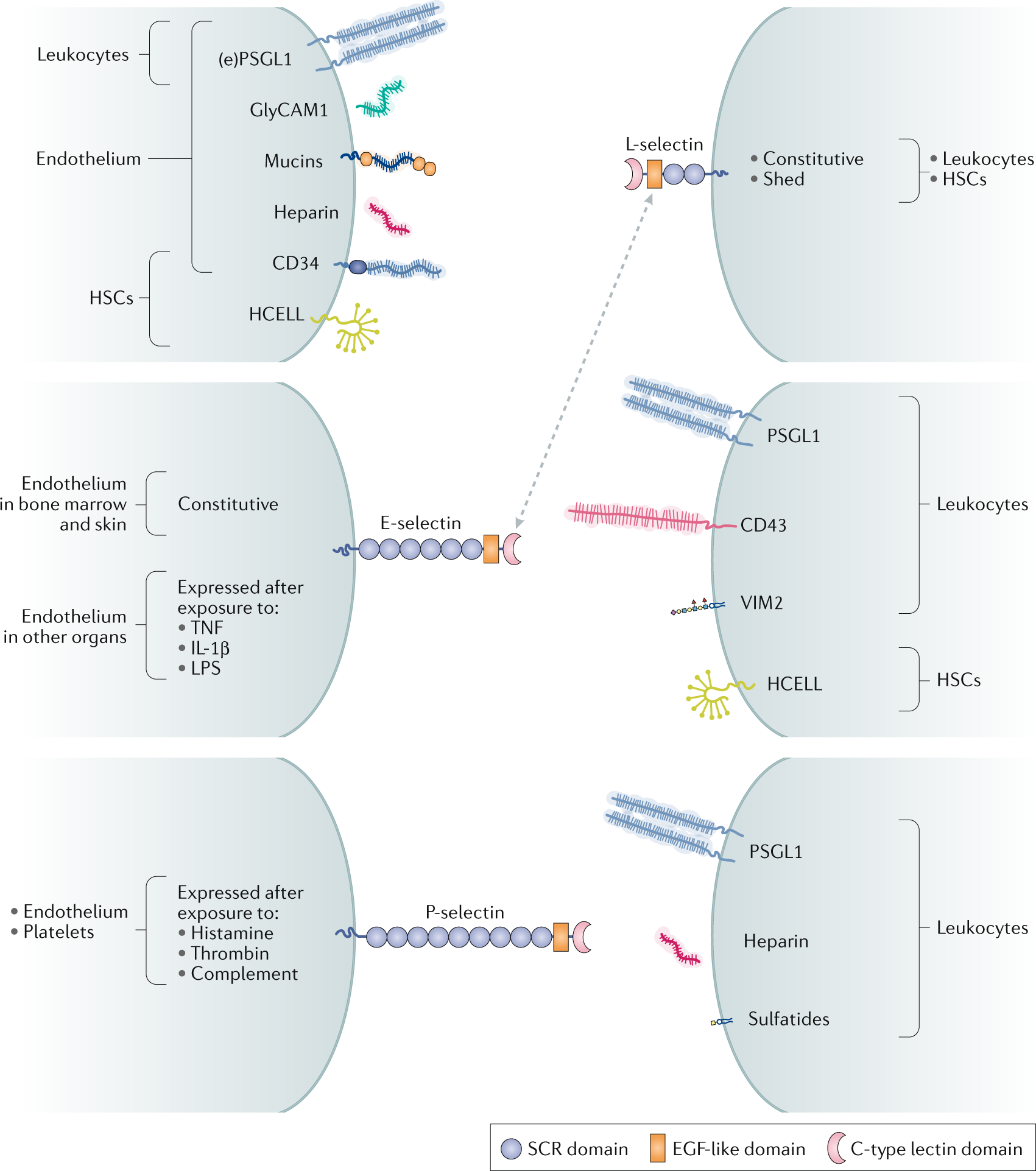
The clinical impact of glycobiology: targeting selectins, Siglecs and mammalian glycans

PDF] Morse code based Secured Authentication System using Eye Blink through Haar Cascade and Facial Landmark Algorithm

BlueNoroff Hackers Utilize ObjCShellz Malware to Create Backdoors on Macs
Recomendado para você
-
 Roblox Evade – Free codes (December 2023) - Xfire07 julho 2024
Roblox Evade – Free codes (December 2023) - Xfire07 julho 2024 -
 Roblox Evade Codes (March 2023)07 julho 2024
Roblox Evade Codes (March 2023)07 julho 2024 -
 Roblox: Evade Codes07 julho 2024
Roblox: Evade Codes07 julho 2024 -
 NEW* ALL WORKING CODES FOR EVADE IN 2023! ROBLOX EVADE CODES07 julho 2024
NEW* ALL WORKING CODES FOR EVADE IN 2023! ROBLOX EVADE CODES07 julho 2024 -
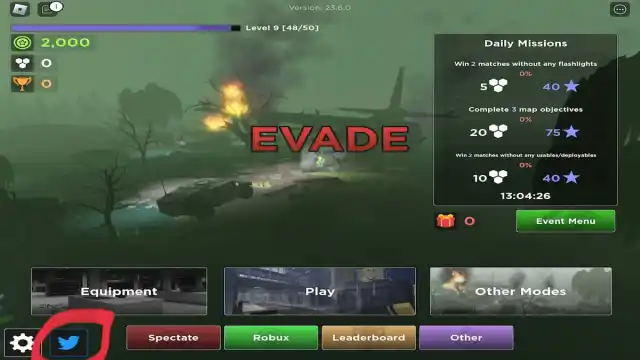 All Evade Codes in Roblox (December 2023)07 julho 2024
All Evade Codes in Roblox (December 2023)07 julho 2024 -
 trooper evade roblox07 julho 2024
trooper evade roblox07 julho 2024 -
 Pro-Palestinian social media users turn to algospeak to avoid07 julho 2024
Pro-Palestinian social media users turn to algospeak to avoid07 julho 2024 -
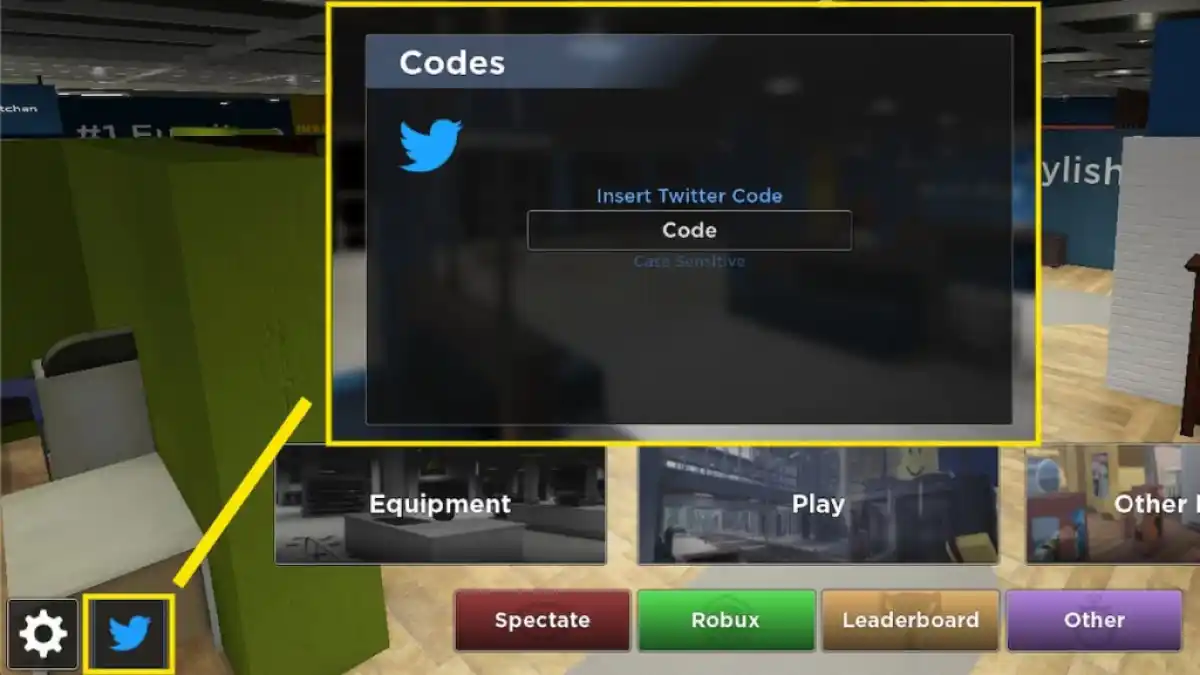 Codes d'évasion (novembre 2022) – Guides de jeu professionnels07 julho 2024
Codes d'évasion (novembre 2022) – Guides de jeu professionnels07 julho 2024 -
 QR Code' Surge in Popularity Brings Along a Rise in QR-Linked07 julho 2024
QR Code' Surge in Popularity Brings Along a Rise in QR-Linked07 julho 2024 -
 BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis07 julho 2024
BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis07 julho 2024
você pode gostar
-
 🔥 Virtual rs MBTI Personality Type - Internet07 julho 2024
🔥 Virtual rs MBTI Personality Type - Internet07 julho 2024 -
 Portal del Profesor - Música - Jogos cooperativos - Desafios07 julho 2024
Portal del Profesor - Música - Jogos cooperativos - Desafios07 julho 2024 -
 MAG PS3 Seminovo07 julho 2024
MAG PS3 Seminovo07 julho 2024 -
project brick bronze forever|TikTok Search07 julho 2024
-
 All Secret slayers unleashed Codes 202307 julho 2024
All Secret slayers unleashed Codes 202307 julho 2024 -
![Animated CD Mayu Kudo / Precure 5, Full Throttle GO GO! [with DVD] Anime Yes! Precure 5 GoGo! Opening Theme, Music software](https://cdn.suruga-ya.com/database/pics_light/game/120048633.jpg) Animated CD Mayu Kudo / Precure 5, Full Throttle GO GO! [with DVD] Anime Yes! Precure 5 GoGo! Opening Theme, Music software07 julho 2024
Animated CD Mayu Kudo / Precure 5, Full Throttle GO GO! [with DVD] Anime Yes! Precure 5 GoGo! Opening Theme, Music software07 julho 2024 -
 Sonic Mania : Video Games07 julho 2024
Sonic Mania : Video Games07 julho 2024 -
 Penalty Shootout - Toys At Foys07 julho 2024
Penalty Shootout - Toys At Foys07 julho 2024 -
 Pixilart - Roblox meme #1 by Jake-d-demon07 julho 2024
Pixilart - Roblox meme #1 by Jake-d-demon07 julho 2024 -
 Roblox Squid Game SECRET CODES07 julho 2024
Roblox Squid Game SECRET CODES07 julho 2024
