Malware analysis Malicious activity
Por um escritor misterioso
Last updated 05 julho 2024
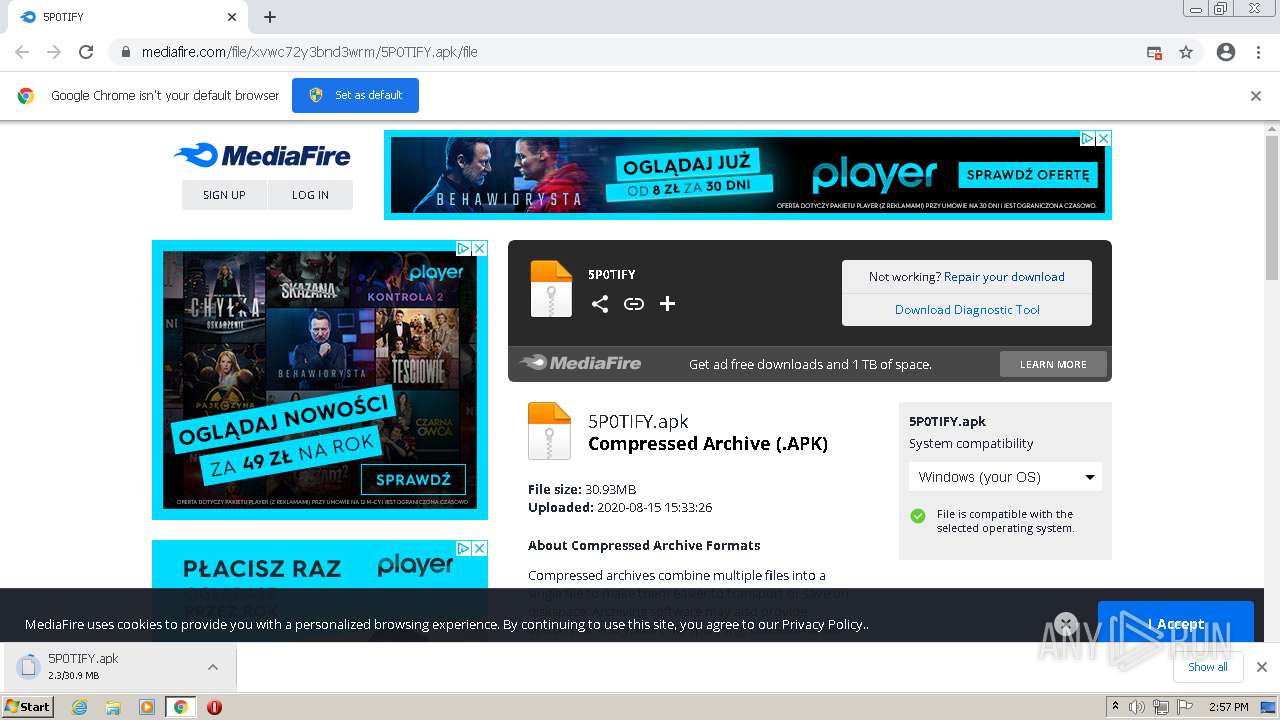

Malware Analysis: Steps & Examples - CrowdStrike
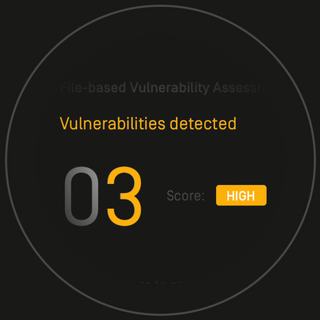
MetaDefender Cloud Advanced threat prevention and detection
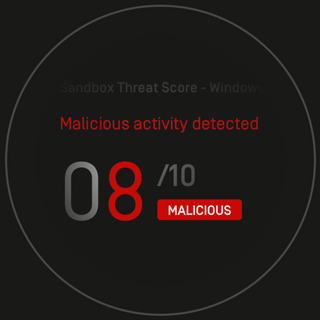
MetaDefender Cloud Advanced threat prevention and detection
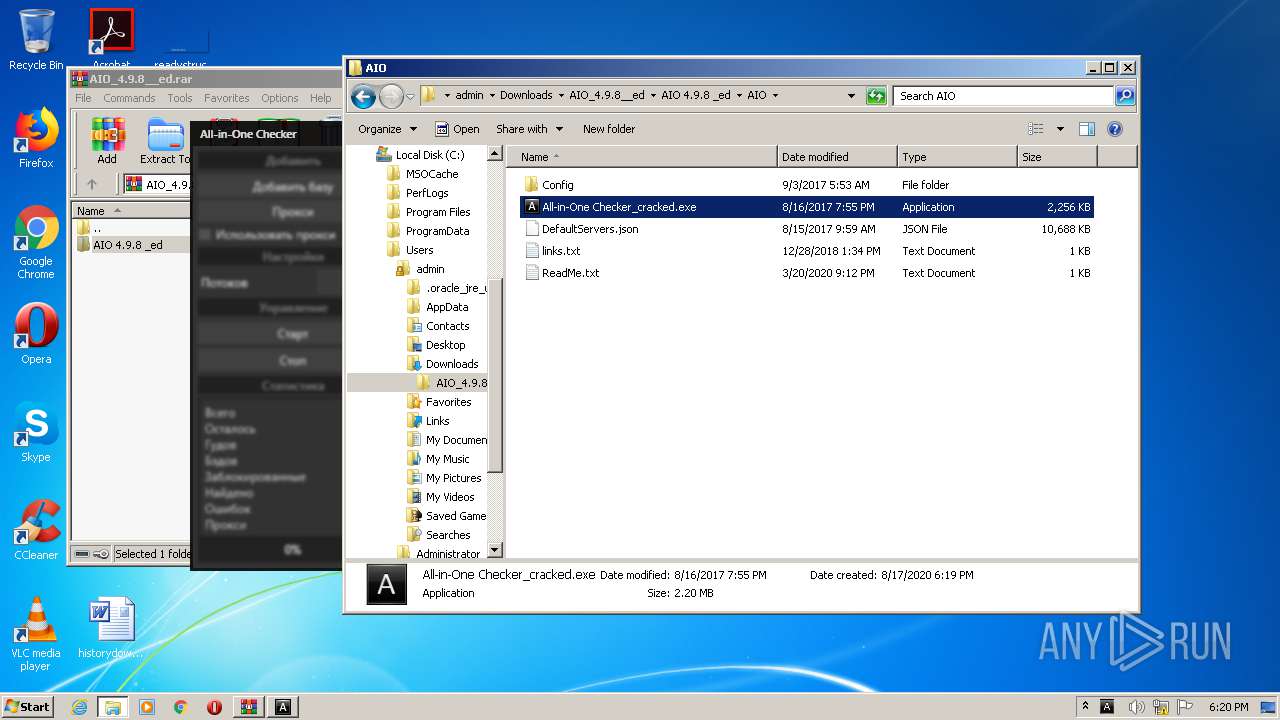
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware leveraging public infrastructure like GitHub on the rise - Security Boulevard

Mastering Malware Analysis
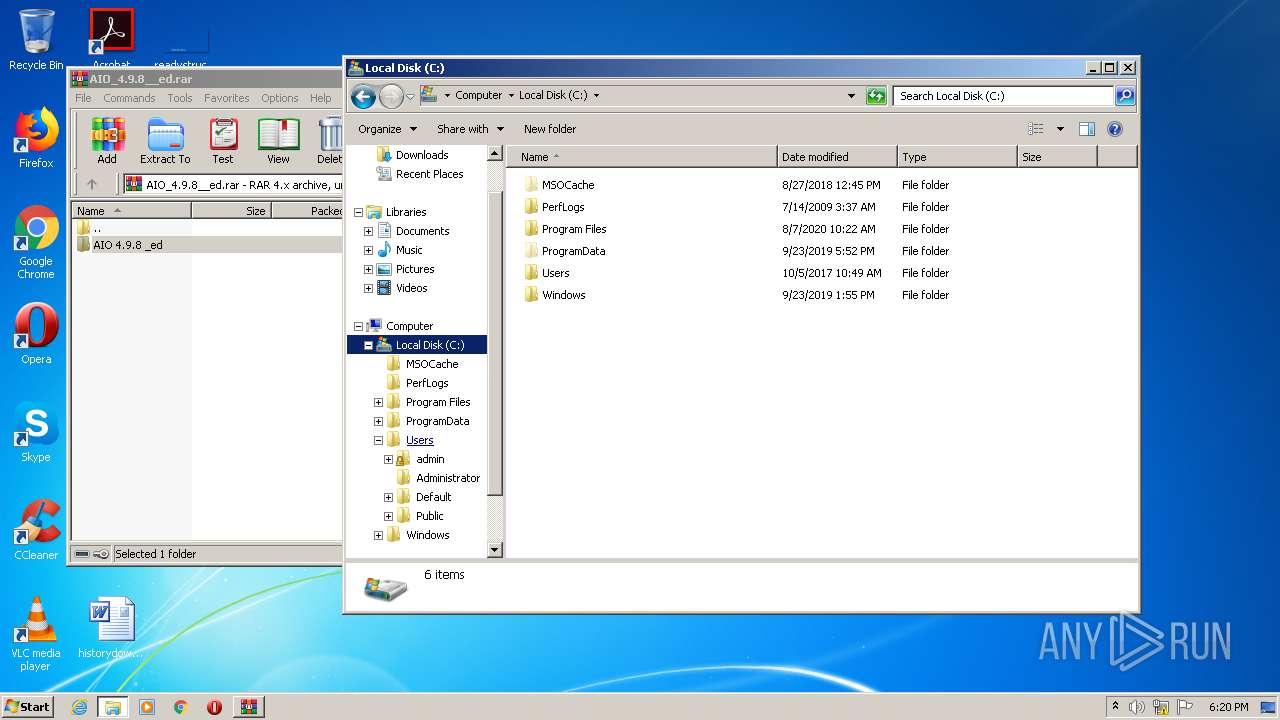
Malware analysis AIO_4.9.8__ed.rar Malicious activity

TryHackMe Cyber Security Exercises and Labs

Brute Force Attacks: Password Protection

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

The Guide to Ransomware Solutions in 2023 - Security Boulevard
Recomendado para você
-
 Lista nowości w Player.pl 01.11.202105 julho 2024
Lista nowości w Player.pl 01.11.202105 julho 2024 -
 Player - nowe filmy, seriale i programy (marzec 2023)05 julho 2024
Player - nowe filmy, seriale i programy (marzec 2023)05 julho 2024 -
 Nowości w abonamencie lub do wypożyczenia na Player.pl 26.03.202305 julho 2024
Nowości w abonamencie lub do wypożyczenia na Player.pl 26.03.202305 julho 2024 -
 Player z mniejszą stratą do Disney+ i HBO Max, Prime Video przed05 julho 2024
Player z mniejszą stratą do Disney+ i HBO Max, Prime Video przed05 julho 2024 -
Nowości SOLIDWORKS 2015 - Szyk łańcuchowy komponentów on Vimeo05 julho 2024
-
 HBO Max z długą listą wrześniowych nowości. Tych produkcji nie05 julho 2024
HBO Max z długą listą wrześniowych nowości. Tych produkcji nie05 julho 2024 -
![NAMM'18: Fender i akustyczne nowości [VIDEO]](https://www.infogitara.pl/img/artykuly/958w/fender-malibu-newporter-redondopm-2e-pm-4ce-paramount-california-player-california-special-california-classic-49725.webp?1682109256) NAMM'18: Fender i akustyczne nowości [VIDEO]05 julho 2024
NAMM'18: Fender i akustyczne nowości [VIDEO]05 julho 2024 -
_61e6eb5678fcf.jpeg) Player reaguje na sytuację w Ukrainie. Bajki po ukraińsku oraz05 julho 2024
Player reaguje na sytuację w Ukrainie. Bajki po ukraińsku oraz05 julho 2024 -
Player Grudzień 2022 – filmy, seriale i programy. Jakie nowości i premiery? - Co za tydzień05 julho 2024
-
 Oglądajcie VOD póki was stać, bo tak szybko drożeje. Cena Playera05 julho 2024
Oglądajcie VOD póki was stać, bo tak szybko drożeje. Cena Playera05 julho 2024
você pode gostar
-
 Site com domínio 'flaviobolsonaro.com' vira plataforma de aposta em jogos - ISTOÉ Independente05 julho 2024
Site com domínio 'flaviobolsonaro.com' vira plataforma de aposta em jogos - ISTOÉ Independente05 julho 2024 -
 The Rock Makes Reference To Classic BYU/Miami Game In TV Sitcom05 julho 2024
The Rock Makes Reference To Classic BYU/Miami Game In TV Sitcom05 julho 2024 -
 Pteranodon/pterodactyl Dinosaur SVG PNG JPG Clipart (Download Now05 julho 2024
Pteranodon/pterodactyl Dinosaur SVG PNG JPG Clipart (Download Now05 julho 2024 -
 Comprei o jogo consim3 agora não abre mais,pede para verificar a05 julho 2024
Comprei o jogo consim3 agora não abre mais,pede para verificar a05 julho 2024 -
 The Elder Scrolls Online Collection: Blackwood (PS4) : Video Games05 julho 2024
The Elder Scrolls Online Collection: Blackwood (PS4) : Video Games05 julho 2024 -
 Feb 3, LIVE WIRE The Ultimate AC/DC Experience05 julho 2024
Feb 3, LIVE WIRE The Ultimate AC/DC Experience05 julho 2024 -
 The workshop allows you to sort by top of one month, by changing05 julho 2024
The workshop allows you to sort by top of one month, by changing05 julho 2024 -
 ThePuffyOne05 julho 2024
ThePuffyOne05 julho 2024 -
 Flag of Finland - Wikipedia05 julho 2024
Flag of Finland - Wikipedia05 julho 2024 -
 Anime Facts Curators - Ging Freecss took the 267th hunter exam and05 julho 2024
Anime Facts Curators - Ging Freecss took the 267th hunter exam and05 julho 2024